When it comes to developing a successful cybersecurity strategy, the volume of threats and vulnerabilities that cybersecurity professionals witness daily can make it difficult to look at the big picture. To see through the flood of sensitive information and alerts, organizations depend on proactive threat intelligence to help them comprehend and downplay cybersecurity risks. Simply put, looking at long-term trends can also aid organizations to make effective yet firm decisions for providing resources to keep at bay denting breaches, irreparable attacks and ransomware.

This is something we can learn from the latest IBM X-Force Threat Intelligence Index 2020 report. The report displays an overview of the noticeable cybersecurity risks of the past years and the threat landscape. IBM’s annual X-Force report 2020 is based on an analysis of data from 70 billion of IBM security events per day spread across over 130 countries. Also, the data collected was analyzed by IBM’s multiple sources, including X-Force Red, X- Force IRIS, publicly disclosed data breach reports and IBM Managed Security Services to name a few.
What does the IBM X-Force Threat Intelligence Index 2020 Report mean?
According to the report, 60% of the early access into victims’ networks that were observed initially took maximum benefit of either known software vulnerabilities or previously stolen login credentials. This allowed attackers to rely less on distraction to gain access. IBM’s report suggests that 2019 was a year that witnessed reemerging old threats/ attacks used in new ways.
As per Wendi Whitmore, VP, IBM X-Force Threat Intelligence, “the frequency of exposed data we are seeing today means attackers are easily getting their hands on more keys to our businesses and private lives. These professional attackers won’t need a lot of time to devise methods into a business or organization. They can execute their attacks by using known information, such as logging in with stolen login credentials”.
Top Initial Attack Vectors: IBM X-Force Threat Intelligence Index 2020
IBM’s latest threat intelligence report highlights the top three initial access vectors in 2019;
- Phishing- At 31%, Phishing was the most aggressively used access vector last year, compared to 50% or less back in 2018.
- Scan and Exploit- Compared to 8% in 2018, exploiting and scanning of vulnerabilities resulted in 30% of such incidents.
- Use of unauthorized credentials has witnessed a boost of 29% as a preferred point of access. Last year saw some of the biggest data breaches where over 8.5 billion records were compromised, resulting in a growing number of stolen credentials that attackers can use.
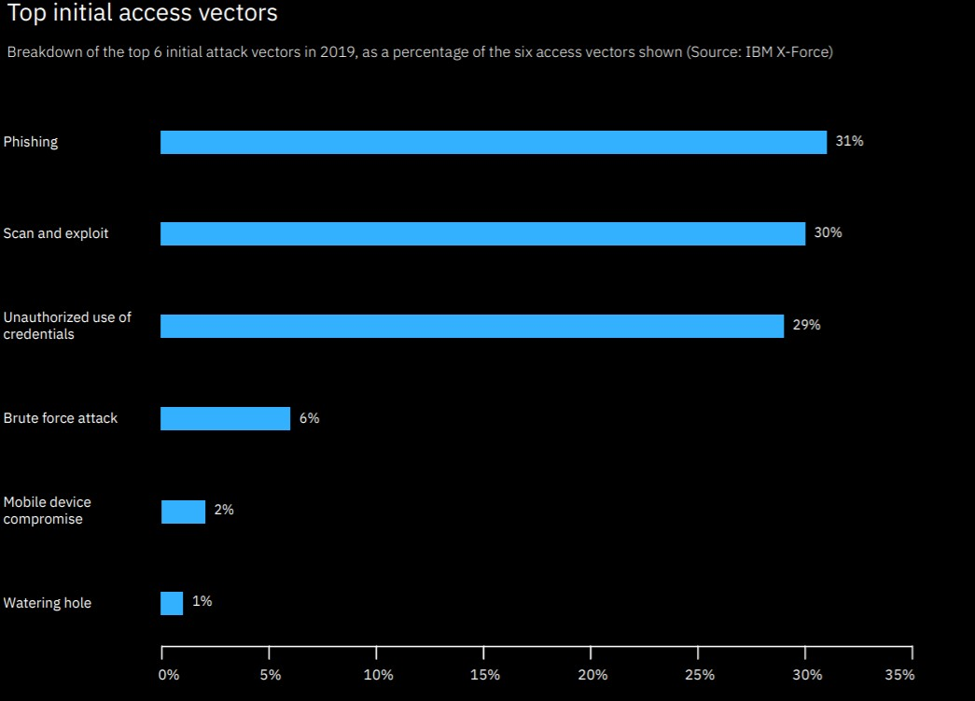
Source- IBM X-Force
Records Breached Grows Significantly
Another key finding of the report- 2019 witnessed ground-shattering breached incidents with over 8.5 billion records out in open. According to the X-Force Threat Intelligence Index 2020 report, the 8.5 billion records exposed were due to miss configurations that jumped to 86% of the records compared to 52 percent in 2018. The significant growth in exposed records across various industries highlights the growing risk of data breaches, even for organizations and industries that are generally not considered prime targets.
Other Key Highlights;
- Some of the top industries loved by attackers include Financial Services, Retail, Transportation, Media, Professional Services, Government, Education, Manufacturing, Energy and Healthcare to name a few. While there was no surprise on the financial services front with 17% of all attacks, it is the retail sector at 16% that has garnered attention by jumping to the second-most attacked industry.
- Most targeted regions- North America, Asia and Europe. X-Force researchers found threat actors targeting across the world, with the highest activity observed in the aforementioned regions. North America, Asia and Europe top the list in all categories comprising 44%, 22% and 21% of the incidents, respectively.
- Phishing continued to be a key threat vector the previous year. According to the X-Force report, the most common and preferred spoofed brands in phishing campaigns were technology and social media platforms. A spoofed website can help fool a user to disclose personal data on a malicious website if it starkly resembles the original. Some of the top spoofed brands include Google, YouTube, Apple, Amazon and Spotify among others.
For similar news and updates on Cybersecurity, visit ExcelliMatrix Blog
ExcelliMatrix will help you to protect your data and reputation. Follow us on Facebook, & LinkedIn or Contact us, 406-646-2102 and get your questions answered.