
Millions of email inboxes are inundated with phishing emails daily. Phishing is so prevalent today that it has become a part of our digital lives. Phishing campaigns were traditionally designed as an easy way for cybercriminals to target credit card or banking credentials. While these traditional phishing methods are still in use today, newer phishing scams target professional email addresses, or online service credentials, which can be used against a wider audience. For a phishing page to be effective, it needs to replicate a legitimate webpage, this way the victim does not realize the deception until it is too late. Creating an effective phishing page does require some web development skills that most inexperienced cybercriminals do not yet possess, so they look for easier alternatives.
What are Phishing Kits?
A phishing kit is used to describe a collection of software tools made specifically for someone with little technical skill to create phishing campaigns. The kits are a complete package containing documentation and manuals that are provided, or sold to cybercriminals, to help them launch their own phishing scams. A phishing kit typically includes website development software that has a simple, low code or no-code graphical user interface (GUI).
Types of Phishing Kits
A common tactic used in phishing attacks is to create a spoofed page of a reputable brand. Cybercriminals can replicate the official page by copying design elements from the legitimate website, so a victim cannot distinguish the spoofed page from the original.
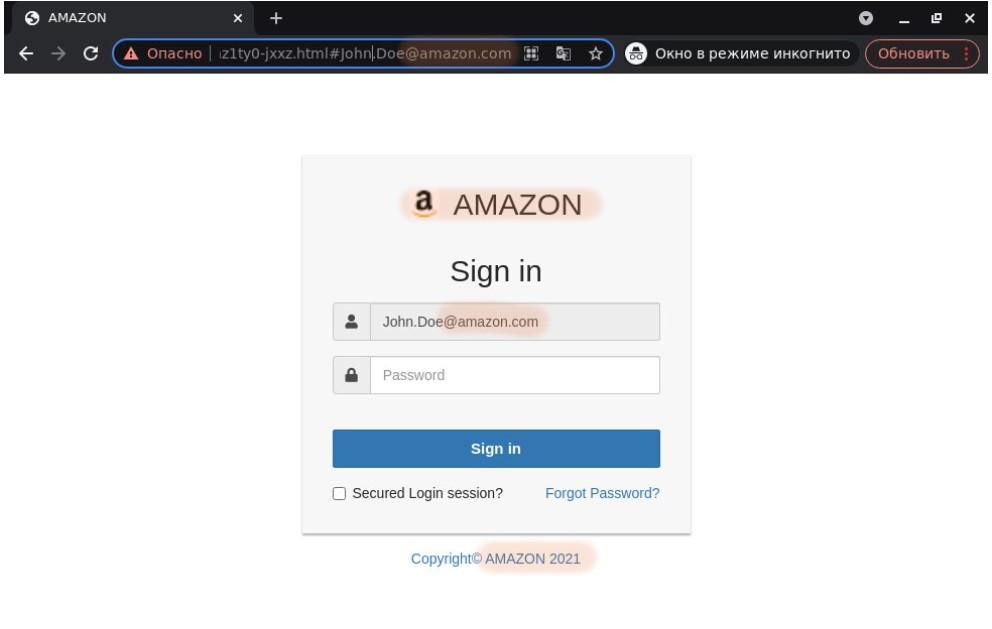
Source- Securelist by Kaspersky
There are many available options of phishing kits available in the market today, with even more being created at an increasingly alarming rate. However, most of them can be categorized into a few types, based on intended targets and their functionality.
Basic
The most basic of the phishing kits are comprised of only a single webpage. They utilize scripts to either store the stolen data or send the data to a remote location using a third-party communication platform like email or Telegram.
Puppeteer
These kinds of phishing kits are designed to phish for online banking credentials and allow indirect or live, interactions between the attacker and the victim. This allows the attacker to prompt their target for more information to bypass security measures and gain access to the online banking accounts. The puppeteer phishing kit can be used to override OTP prompts, secret words, or even security phone calls.
Dynamic
Dynamic Phishing kits contain specially developed code and logic to present specific content to the target. It can appear in the form of introducing a spoofed consumer banking login portal based on previous input and even display logos of specific companies based on the victims’ email addresses.
Commercial Kits
Most of the sought-after phishing kits have been commoditized, with the authors licensing usage of the kits and providing online storefronts. If you know where to look, you can log in, purchase, and download these phishing kits. FreakzBrothers and 16Shop are a couple of the known examples that provide commercial phishing kits.
Why Phishing Kits?
Phishing kits make conducting phishing campaigns easier for both experienced and inexperienced cybercriminals. Phishing pages are regularly reported to hosting providers and are quickly shut down. Phishing kits make it possible to host multiple spoofed phishing pages, which enables the attacker to utilize a variety of sites for a wider range of targets.
Some phishing kits offer anti-detection systems. They are configured to reject incoming connections from known bots for search engines, security firms, or other anti-phishing organizations. Once the phishing page is indexed by a search engine like Google, the phishing page is taken down or blocked almost immediately after detection. Some phishing kits also utilize geolocation and can swap languages based on the victims originating IP, making them even more difficult to identify.
Users should avoid clicking on links or attachments in emails from unknown senders or any other communication platforms, such as WhatsApp and Telegram. SMS on mobile phones is also susceptible to these attacks and may also contain phishing links. Report phishing emails to your IT department or service provider. This will help prevent others from falling victim to the same scam.
Follow us on Facebook, & LinkedIn or Contact us at 406-646-2102 and get your questions answered.