Cybersecurity research at Proofpoint, a cybersecurity company based out of California that specializes in phishing and social engineering defense, recently released an article covering a long running social engineering and malware campaign that targeted aerospace and defense contractors. Run by state-aligned Iranian threat actors operating under the handle “TA456,” the attack focused on building trust with specific targets through email and SMS conversations under a well-crafted media persona posing as an aerobics instructor named “Marcella Flores,” before eventually delivering malware through email attachments. The attachments are highly personalized documents thick with macros, the malware itself is an updated version of “Liderc.” Researchers at Proofpoint have named this new variant “LEMPO.” The LEMPO malware performs reconnaissance on the infected machine, gathering and saving as much data as it can before exfiltrating said data to an email account via SMTPS, and then covers its own tracks.
Activity on the fake social media profile extends back to 2018, where not long after the “Marcella” profile began friending individuals who publicly identified as defense contractors living around the same area as the false personality. Going years without being discovered is proof of the persistence and effort that goes into these targeted phishing campaigns.
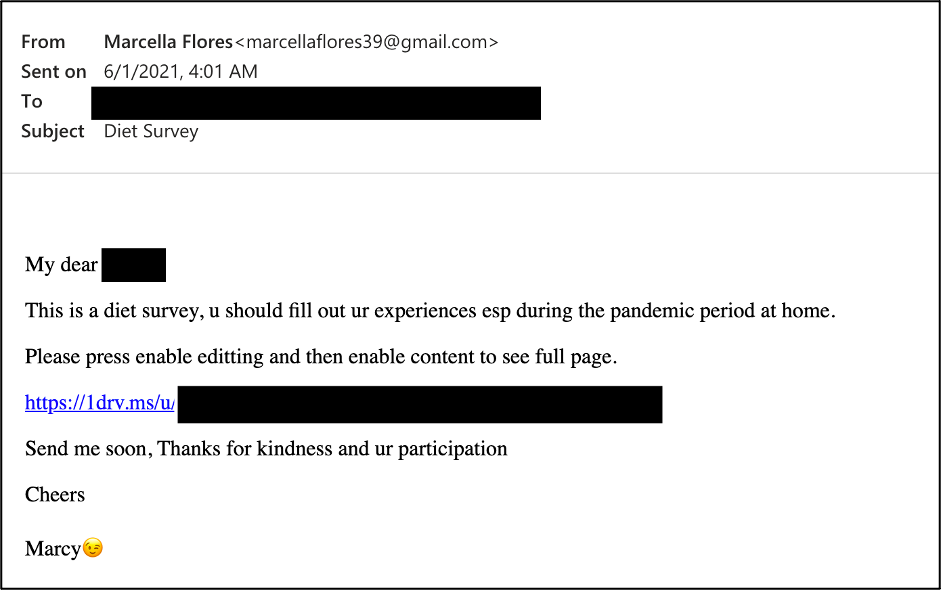
Source- Proofpoint
“Marcella” would regularly update their profile with new pictures, statuses, and even videos while sending out flirtatious emails containing benign videos, links, and regular communication. After spending enough time becoming familiar with their target, the threat actors would send a OneDrive URL that delivered a zipped .rar file. The .rar would include a highly personalized excel spreadsheet that requested the user enable content. Should the user do so, the macros embedded in the spreadsheet create a hidden directory and write out the LEMPO malware in plaintext. Since enabling content would allow it to run Visual Basic Script, a registry key is also added to force LEMPO to run at login. LEMPO would then gather a large swath of information such as:
- Date and time
- Hostname, username, and password information
- System Information (firewall rules, running processes, IP information, domains, etc.)
- Antivirus information
- Drive information
- Software information (Such as VPNs)
As the information was gathered, it would be saved to a “Logs.txt” file, to later be zipped and sent back to the attacker.
This cyber-espionage group has been involved in similar social engineering attacks, using the same spoofed social media profiles of attractive women to coax potential targets into downloading their malware. Facebook took the “Marcella Flores” profile down this month after it was identified along with other similar accounts. The social media giant has linked the malware used in this campaign to an Iranian IT firm with connections to the Islamic Revolutionary Guard Corps (IRGC).
This “Marcella Flores” campaign and other similar campaigns denote how social engineering can be a worthwhile attack for government threat actors. Try not to forget the importance of being watchful of what we share on social media platforms, and who we share it with. It is more crucial for those working within the defense industry to be mindful of who they’re communicating with, be it via work or personal accounts. Threat actors often exploit publicly available information about their targets to create completely new personas to carry out cybersecurity attacks. Oversharing on social media platforms is incredibly risky if one works in a sensitive field.
Complete report: https://www.proofpoint.com/us/blog/threat-insight/i-knew-you-were-trouble-ta456-targets-defense-contractor-alluring-social-media#
For more news and updates, visit https://blog.excellimatrix.com/
You can also reach us out on Facebook, & LinkedIn or Contact us