
Google’s Threat Analysis Group (TAG) has recently released information regarding four zero-day vulnerabilities that have been exploited as of June of this year. Zero-day vulnerabilities are previously unknown vulnerabilities that can be exploited by attackers until they are identified and patched. Google’s TAG and Project Zero researchers found that the four zero-days were used in a broader targeted malware campaign that exploited previously unknown flaws in Internet Explorer and WebKit- browser engines used by both Safari and Google Chrome.
The four zero-day exploits are now included in the Common Vulnerabilities and Exposures (CVE) database and are identified as CVE-2021-21166, CVE-2021-30551, CVE-2021-33742, and CVE-2021-1879. The two exploits that affect Google Chrome, CVE-2021-21166 and CVE-2021-30551 were discovered in February and June of 2021. Both zero-day exploits were exploited through one-time links sent by emails to specific targets, all of whom are believed to be in Armenia. The one-time links led these victims to a hacker-controlled domain and website that resembled a legitimate website. Upon clicking the link, the targeted users were redirected to a page that would collect device information, generate ECDH keys to encrypt the exploits, then finally send the collected data back to the exploited server.
With CVE-2021-33742, the Internet Explorer exploit, Google’s TAG researchers discovered a campaign back in April and in June of 2021. This also targeted Armenian users, but with malicious Office documents that loaded web content within Internet Explorer. The researchers believe this happened by either spawning an Internet Explorer process via VBA macros to navigate to a web page or embedding a remote ActiveX object using a Shell.Explorer.1 OLE object.
WebKit CVE-2021-1879 was discovered by Google’s Threat Analysis Group on March 19, 2021. This exploit is believed to be used by Russian-backed actors and utilized the LinkedIn messaging platform to target government officials from western European countries. The attackers would send malicious links and if opened from an iOS device, the targeted user would be redirected to a domain controlled by the attackers.
Google’s TAG and Project Zero researchers also noted that 2021 has seen a large rise in zero-day attacks. Only halfway into 2021, and already there have been 33 zero-day exploits utilized in recent attacks.
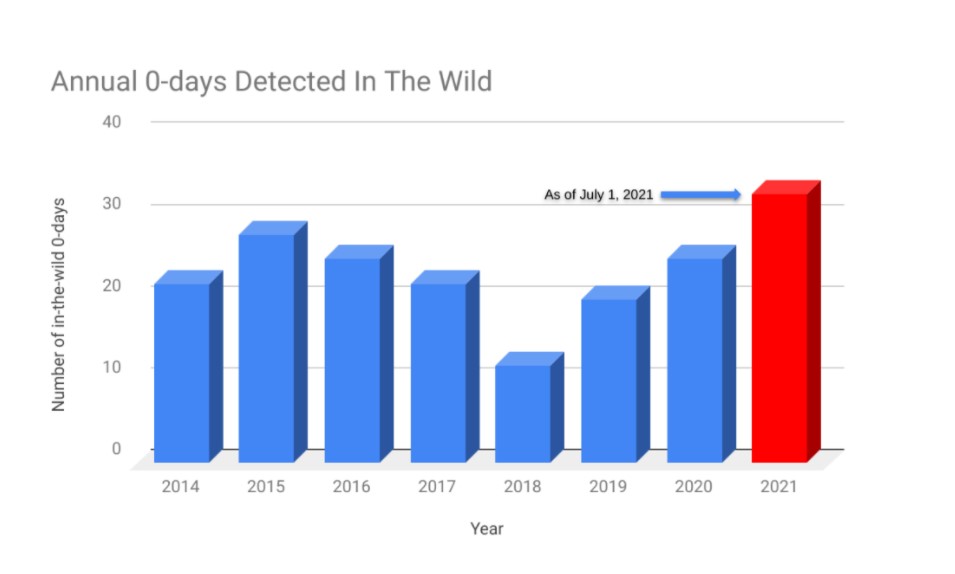
Source - Google TAG
Google believes the increase in zero-days is due to better detection and disclosure efforts, but also because of the expansion of commercial vendors and third-party vendors selling access to zero-day vulnerabilities. In mid-2010, many private companies started selling zero-day capabilities in the marketplace. In days past, groups needed to have technical skills, now it is resources over expertise. Three of the four zero-days that TAG discovered this year are in this category, created by commercial providers, sold to, and used by government-backed actors.
In addition, the report also discusses a few reasons as to why attackers are utilizing more zero-day vulnerabilities. First, due to the rapid expansion of mobile platforms, this resulted in a surge of products that attackers want capabilities for. Second, as mentioned previously, commercial vendors selling access to zero-day exploits. Third, with more efforts in improving security, this escalates the need for hackers to utilize zero-day exploits over less complicated means, like phishing and spam.
Google TAG Report: https://blog.google/threat-analysis-group/how-we-protect-users-0-day-attacks/
For more news and updates, visit https://blog.excellimatrix.com/
You can also reach us out on Facebook, & LinkedIn or Contact us