
Google Chrome extensions are a part of daily life and are meant to make life easier. Downloading an extension can be tempting with Chrome browser extensions that can take screenshots, help get the latest discounts, watch TV shows with friends, and correct grammar. However, not all extensions are perfect, as there are popular extensions that put privacy at risk.
According to the McAfee report, these malicious extensions are infected with malware and appear as cookies whenever a user visits any online website. The report also suggests that these identified extensions can track users’ browser activity with every website visit sent to servers owned by the extension creator. The extension creator can then insert affiliate code into eCommerce websites being visited by users and receive an affiliate payment for items the user purchases. The sharing of browsing data implies an implicit breach of privacy for the consumer.
Also Read: Tips to Avoid Mobile Payment App Scams
McAfee cybersecurity researchers highlighted five Google Chrome extensions that may steal your data. The five identified extensions were “Full Page Screenshot Capture- Screenshotting”, “Netflix Party”, “FlipShope- Price Tracker Extension”, “Netflix Party 2”, and “AutoBuy Flash Sales”. This is significantly worrisome since these extensions have over 1. 4 million combined download counts.
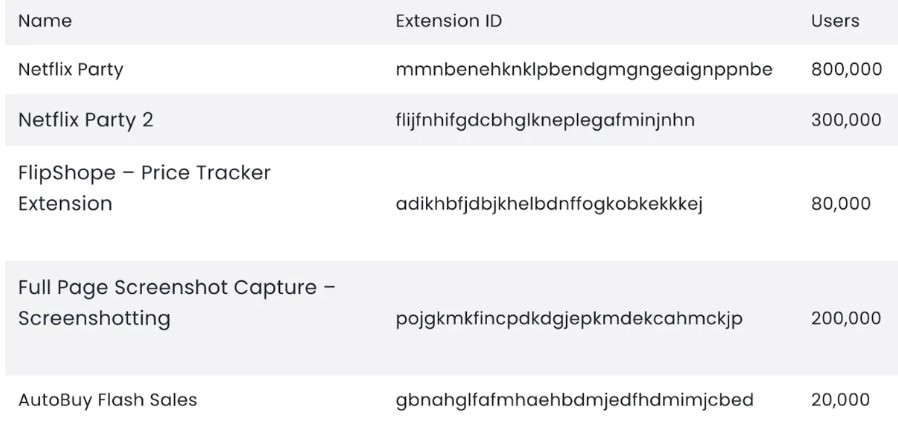
Source- McAfee
These extensions offer different functions, allowing users to take screenshots of websites they visit, get discount coupons, and watch Netflix shows together. It is not the first time “Netflix’s imposter extension” has come under cyber security experts’ radar. McAfee had reported the Netflix Party extension back in March. The report suggests that the malicious extension cloned the original Netflix Party extension that allowed groups of people to watch a show simultaneously. However, only the knock-off version tracks the user’s browser activities. The imposter Netflix Chrome extension duped over 100,000 users spread across Europe, India, and the USA. To make the fake extension appear legitimate, the extension creators created several fake review websites and Twitter accounts.
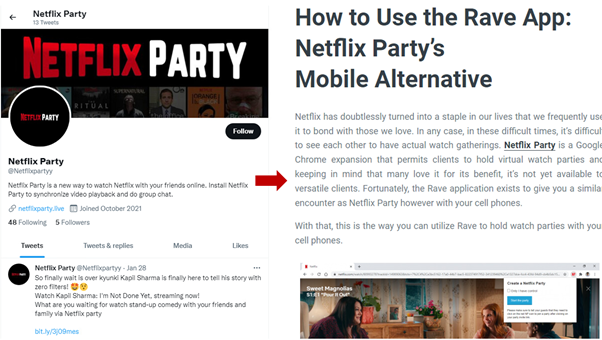
Source- McAfee
A victim may search the web or Twitter for Netflix Party, read the articles, and reviews, and click on a link that will redirect them to the Google Play Store. After the installation and accept the permissions. The victim then performs a web search or directly visits a gift card website; the extension identifies the website and redirects the user to a phishing site. The victim enters their gift card details on the phishing site, and the information is posted to the server to which the malicious actor has access. They can sell or use the stolen data, resulting in the theft of the victim’s funds.
The best way to avoid falling for this scam is to be cautious when tempted to install any new Chrome extension. Experts at McAfee recommend users pay attention to the extension permissions requests that Chrome displays on their screen before installation of the extension. Users should also verify the authenticity of the extension before granting permission.
For more updates on Cybersecurity, Visit https://blog.excellimatrix.com/ or follow us on Facebook & LinkedIn or Contact us at 406-646-2102 and get your questions answered.