
The Kaseya VSA attack is having a ripple effect across more than 1,000 organizations. When the attack came to light earlier this week, Kaseya confirmed that the incident affected a small number of on-premises customers. Given the supply chain nature of Kaseya’s operation shows a whole different story, and it is more likely to have far more organizations affected by the attack. REvil was found to be the group behind the attack, they are also speculated to be responsible for several other high-level ransomware attacks. The ‘Happy Blog’ culprit has been claimed to have infected more than a million systems, and that the data could be decrypted with a universal decryptor. Upon receiving a payment of $70 Million in Bitcoin, the universal decryptor would be publicly published to allow all the victims’ files to be decrypted.
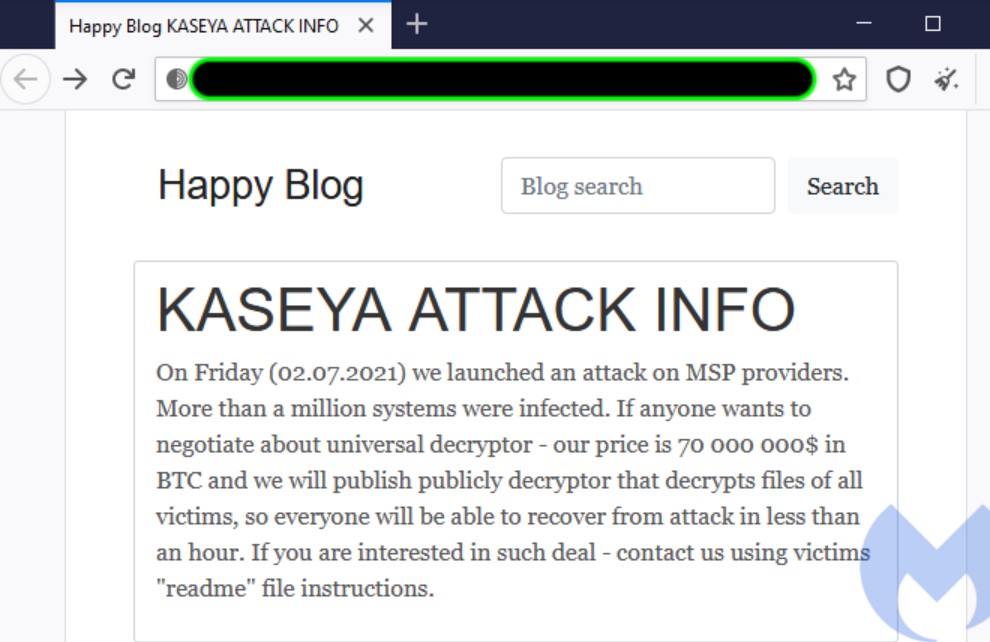
Source: Malwarebytes Labs
In response to the phishing attack, Kaseya took several steps. The IT company asked its customers to shut down its VSA servers immediately. They also notified their customers via email, phone, and in-product notices to shut down their VSA servers. Further, the company also enlisted help from its internal incident response team and outside professionals like Cybersecurity and Infrastructure Security Agency (CISA) and the FBI to learn the incident's root cause. Kaseya also developed a Compromise Detection Tool that can scan VSA servers or managed endpoints to find any compromise indicators (IoC).
Soon after, a Kaseya IT firm suffered from a VSA ransomware attack on July 3rd. It appears that now cybercriminals are taking advantage of the attack and infecting systems with cobalt-strike and other malware. According to the cybersecurity researchers at Malwarebytes, the malicious spam campaign exploiting the Kaseya VSA attack was discovered on July 6th. The phishing email utilized in this campaign asks recipients to install an update from Microsoft to protect against ransomware. This email is also packaged with an attachment ‘SecurityUpdates.exe’, however, anyone who downloads and installs the attachment is infected with Cobalt-Strike-delivered malware.
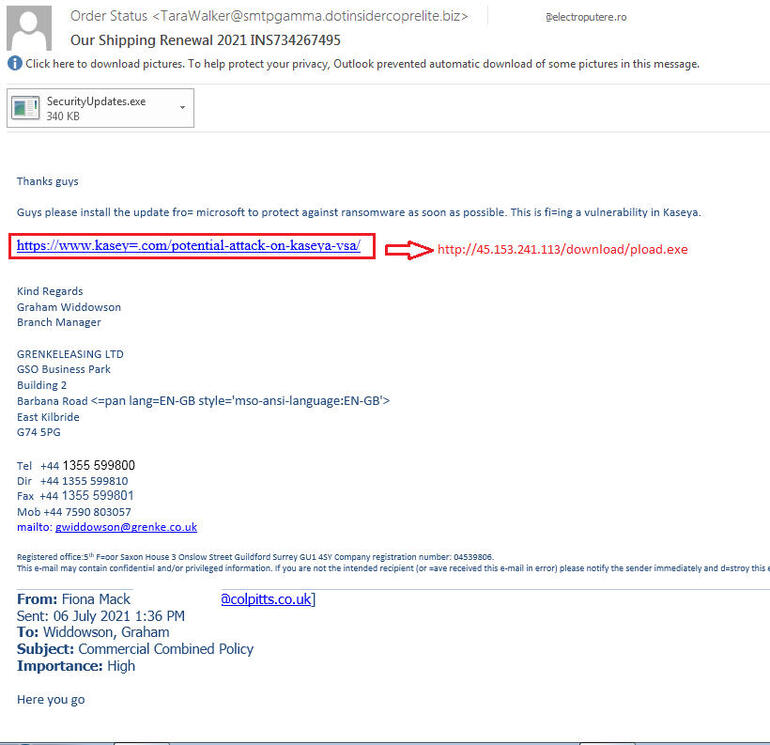
Source- Malwarebytes
Cobalt Strike is designed and intended to be an internal security tool and to be used by organizations to test their internal security for any vulnerabilities. Yet, it has been increasingly used by cybercriminals to deploy malicious payloads into targeted networks and devices. Recently, campaigns have deployed Cobalt Strike as the first payload to deploy future attacks.
In its latest update, Kaseya revealed that they were working on a patch to fix the vulnerabilities in its VSA software. Unfortunately, the company has run into some difficulties. During the VSA SaaS (Software as a Service) deployment, an issue was discovered that blocked the release of the new patch. At the time of writing, there was no update on the availability of the patch. Until the patch release, the company published a list of the changes that their customers should make to their own on-premises environments.
Even the best anti-malware solutions can be tricked by smart binary obfuscation techniques, so it is critical to incorporate training for users to recognize if emails and notifications are legitimate before clicking on attachments or providing confidential, or personal, data. A proactive threat hunting and continuous monitoring solution can provide the proficiency to spot any potentially suspicious activities that may have escaped the initial defense mechanisms in place.
https://blog.malwarebytes.com/cybercrime/2021/07/shutdown-kaseya-vsa-servers-now-amidst-cascading-revil-attack-against-msps-clients/
For more news and updates, visit https://blog.excellimatrix.com/
You can also reach us out on Facebook, & LinkedIn or Contact us